Distributed Denial of Service (DDoS) attacks, which aim to overwhelm systems with excessive traffic, pose a significant threat to the functionality and reliability of medical devices. For critical healthcare environments, downtime or disruptions can have life-threatening consequences. Here’s a comprehensive guide to developing software for medical devices that is resilient to DDoS attacks.
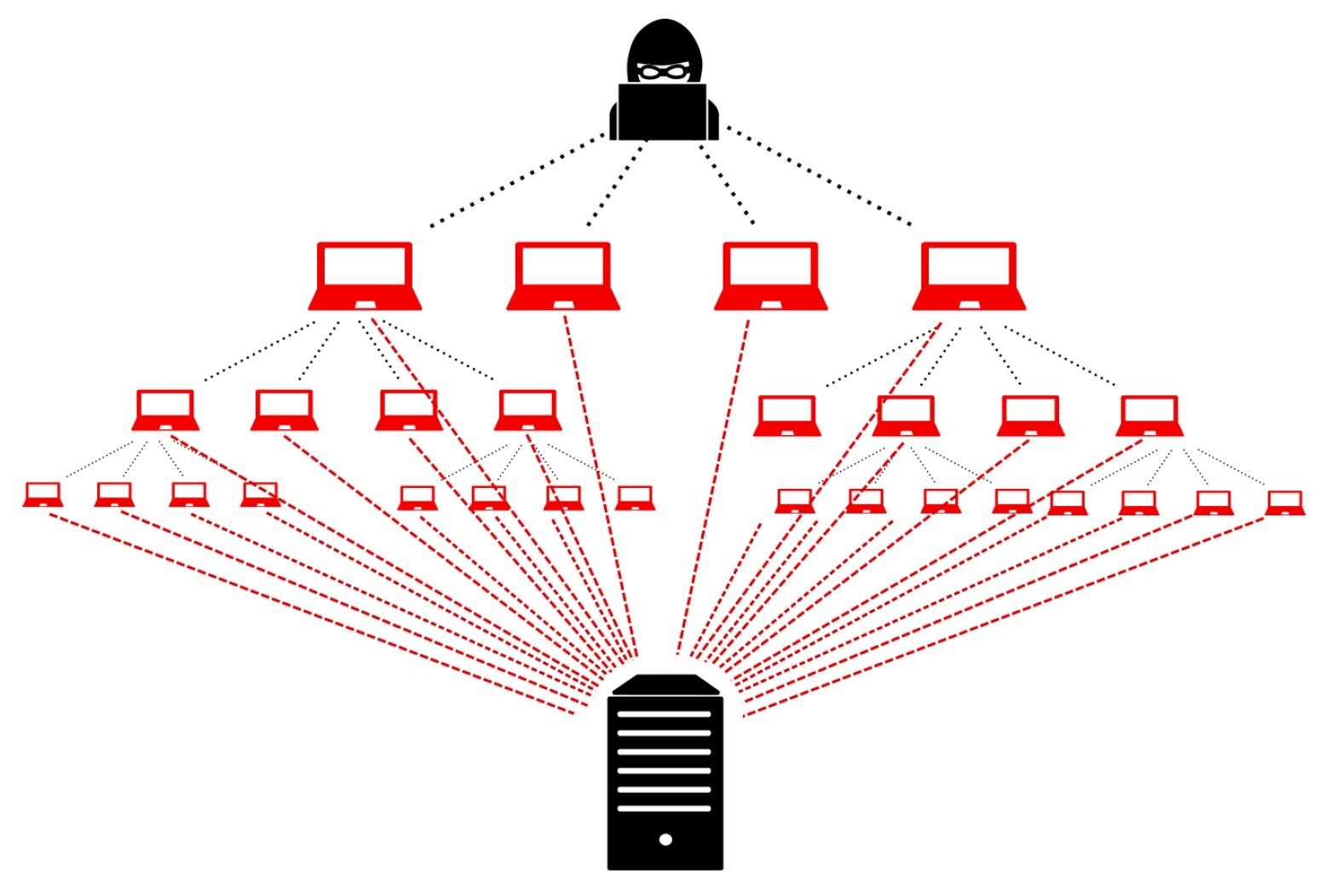
1. Understanding the Threat Landscape
DDoS attacks target vulnerabilities in networked systems, including medical devices. These attacks can:
- Overload servers or cloud-hosted platforms.
- Disrupt device-to-cloud communications.
- Prevent timely access to critical healthcare data.
For medical devices, the stakes are even higher because of their role in patient diagnosis, monitoring, and treatment.
2. Principles of DDoS-Resilient Software Design
To build medical device software resilient to DDoS attacks, consider the following principles:
a. Minimal Attack Surface
- Use the least privilege approach to limit access to critical functions.
- Disable unused ports and services to reduce potential entry points.
b. Robust Network Protocols
- Implement rate limiting to control traffic volumes.
- Use secure and authenticated protocols like TLS for device communication.
- Employ load balancing to distribute traffic efficiently.
c. Scalability
- Design software to scale horizontally, ensuring the system can handle traffic surges.
- Leverage cloud-based infrastructure with built-in DDoS mitigation services.
d. Redundancy and Failover
- Establish redundant systems to ensure continued functionality during an attack.
- Enable automatic failover to alternate systems or networks when primary resources are compromised.
3. Integrating DDoS Mitigation Strategies
a. Use DDoS Protection Services
Many cloud providers, such as AWS, Azure, and Google Cloud, offer DDoS protection services tailored to medical device software needs. These services can detect and mitigate attacks before they impact device operations.
b. Network Traffic Analysis
- Implement real-time monitoring tools to identify unusual traffic patterns.
- Use machine learning to detect and respond to anomalies proactively.
c. Secure APIs
- Limit API request rates to prevent abuse.
- Authenticate API access using tokens or keys.
d. Data Prioritization
- Assign higher priority to critical data packets related to patient care.
- Deprioritize or block non-essential traffic during an attack.
4. Regulatory and Standards Compliance
Developing DDoS-resilient software for medical devices also involves adhering to regulatory and industry standards:
- FDA Guidance: Follow cybersecurity premarket guidance for device security.
- ISO/IEC 27001: Implement information security management best practices.
- IMDRF Principles: Align with international principles for medical device cybersecurity.
5. Testing and Validation
a. Simulated DDoS Scenarios
- Test your software’s resilience using simulated DDoS attacks.
- Assess performance metrics, such as response times and availability.
b. Penetration Testing
- Conduct thorough penetration testing to uncover vulnerabilities.
- Include DDoS-specific scenarios in your test plan.
c. Continuous Monitoring and Updates
- Monitor software performance post-deployment to identify emerging threats.
- Provide timely updates and patches to address vulnerabilities.
6. Collaboration and Knowledge Sharing
Cybersecurity is a shared responsibility. Collaborate with:
- Cloud Providers: Ensure their infrastructure supports DDoS mitigation.
- Healthcare Facilities: Educate users about best practices.
- Industry Peers: Share insights and learnings to improve collective resilience.
Conclusion
Developing DDoS-resilient software for medical devices is not just a technical challenge; it’s a critical responsibility to safeguard patient safety and healthcare continuity. By adopting robust design principles, leveraging advanced technologies, and adhering to regulatory standards, medical device manufacturers can build resilient systems capable of withstanding DDoS attacks. Prioritizing cybersecurity from the outset is the key to enabling trust and reliability in interconnected medical devices.
